Check out this blog article from Intelligens Consulting, looking at the risks of implementing IoT and how to help prevent these.
In the first half of 2021 there were over 1.5 billion IoT related cyber security attacks, more than double the previous year. Many of these attacks exploit device vulnerabilities and can expose individuals lead to reputational damage and financial loss for businesses. This article asks what risks arise from the increasing number of connected devices and what security design considerations can be used to prevent them.
The numbers are startling
Cybersecurity expert Kaspersky estimates that over 1.5 billion IoT security breaches occurred worldwide in the first half of 2021. That means over 1 in 5 IoT devices suffered from a security breach in 2021.
While this may seem a staggering number, what’s more startling is that this represents a 136 percent increase in IoT security breaches compared to the previous year and it is likely to get worse before it improves due to the significant continued growth in IoT device deployment.
To put these numbers into context, in the UK alone, we estimate that some 55 million IoT devices out of an install base of 253 million were comprised compared to just 1,324 cybersecurity incidents in 2021.
These figures show that IoT security breaches dwarf regular forms of cybersecurity breaches making IoT cybersecurity the number one concern for users, manufacturers, service providers and policy makers.
What do these attacks look like?
Almost three out of five IoT security breaches leveraged telnet – a computer protocol that was built for interacting with remote computers and can be used to connect to open ports.
As a result, individuals are exposed to threats such as invasion of privacy, physical and psychological harm, while cyber-attacks on businesses can lead to reputational damage and financial loss.
A study carried out the Department for Digital, Culture, Media & Sport (DCMS) in early 2020 looking into IoT cyber security vulnerabilities shows how one attack using malware cracked default passwords on security cameras and DVRs connected to public Wi-Fi networks by exploiting an open telnet server. In addition to gaining unauthorised access to personal video footage, the attacker was able to spread further malware, mine bitcoin and launch DDOS attacks.
In another example the owner of a popular smart doorbell found out that his ex-partner had been accessing and downloading video from his smart doorbell to monitor his activities and physically abuse the individual.
Its not just consumers but businesses that are also affected according to the study.
An architecture firm using smart (internet connected) drawing pads became vulnerable due to poor security practices which were exploited by attackers to hack devices and launch DDOS attacks overwhelming the firm with vast amounts of requests for information.
The study also shows how vulnerable the power grid can be because attackers exploit vulnerabilities in smart home appliances such as TVs, refrigerators and washing machines for example.
Many cybersecurity breaches are a result of attackers being able to exploit vulnerabilities in IoT devices, routers and cameras for example. This is proliferated because of poor password hygiene or IoT devices unable to receive security updates once they have left the factory floor.
What is being done about it?
From a policy perspective the UK Government in November 2021 introduced the Product Security and Telecommunications Infrastructure bill (PST) in Parliament which (scheduled for a third reading in the Commons later this year).
The bill will ban default passwords and will require manufacturers to disclose the minimum amount of time a product will receive vital security updates.
The bill if passed requires IoT manufacturers, importers, and distributors of smart connected products to meet best practice cybersecurity standards. However, the bill does not cover routers, connected vehicles, smart meters, medical devices and desktop and laptop computers which seems to be a critical set of omissions.
IoT security however should not be limited to devices. Communications networks need to have access controls, firewalls and end-to-end encryption to distribute device generated data securely. Analytics platforms and cloud applications require multi-factor-authentication to protect against data theft.
To this end global standards body the International Telecommunications Union’s (ITU’s) Study Group 17 is working on the security of IoT applications and services including smart grids, cloud computing, financial systems, distributed ledger technology, intelligent transport systems and eHealth.
What should you do about it?
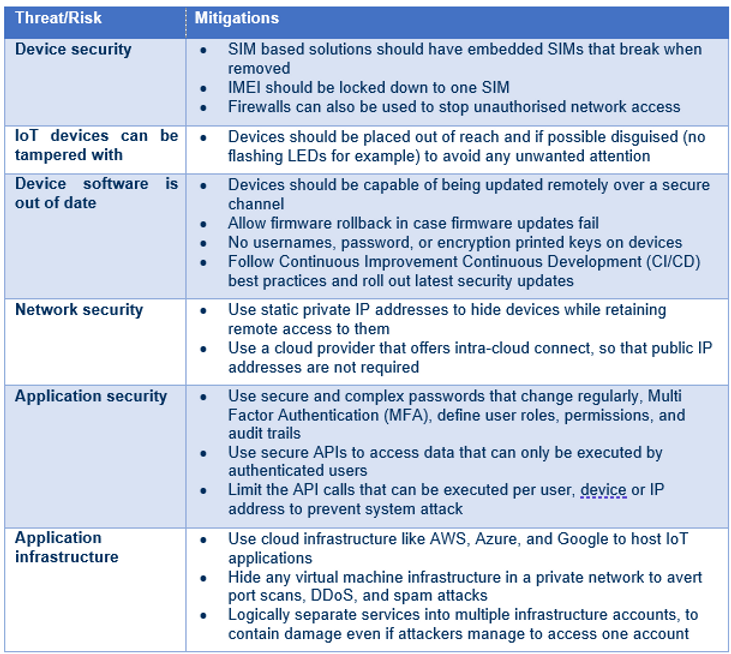
Whether you are a local authority or an enterprise there are several steps you can take to secure your IoT platform from increasing security on the device, enhancing network security and ensuring the application is secure. The table below provides a list of potential risks and mitigations that can be taken.